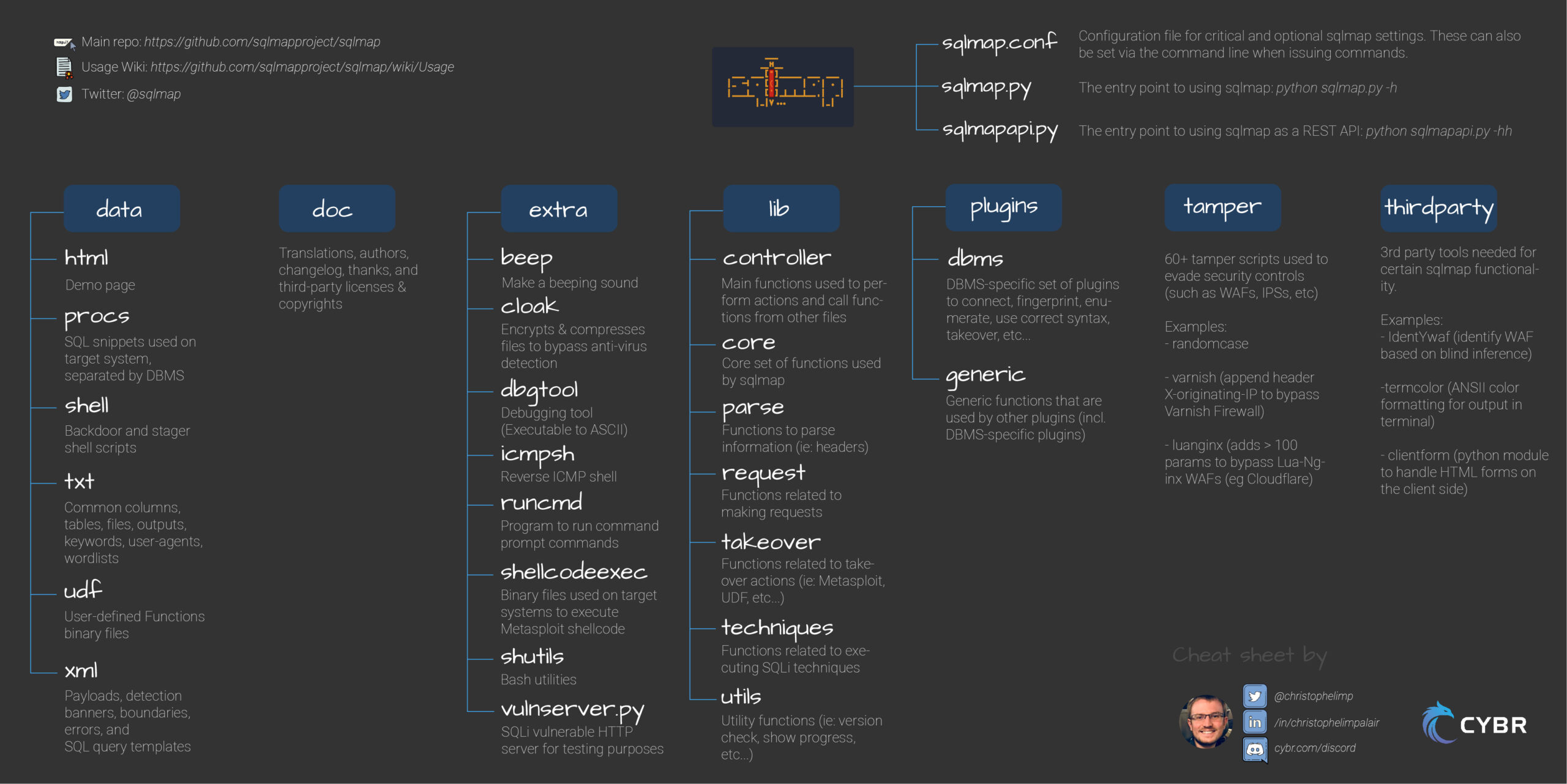
Sqlmap Cheat Sheet - It covers installation, basic usage, ip address. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to.
It covers installation, basic usage, ip address. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities.
Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to. It covers installation, basic usage, ip address. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities.
Sqlmap Cheat Sheet Commands, Options, and Advanced Features
Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. It covers installation, basic usage, ip address. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection.
Cheat Sheet Nmap Pdf
A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. It covers installation, basic usage, ip address. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits.
sqlmap Cheat Sheet Commands for SQL Injection Attacks + PDF & JPG
Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. It covers installation, basic usage, ip.
The Practical Guide to sqlmap for SQL Injection Course Cybr
Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to. It covers installation, basic usage, ip.
Sqlmap Cheat Sheet Commands and Flags
It covers installation, basic usage, ip address. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection.
Sqlmap Cheat Sheet PDF
Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. It covers installation, basic usage, ip address. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection.
Sqlmap Cheat Sheet Commands, Options, and Advanced Features
A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. It covers installation, basic usage, ip address. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits.
sqlmap Cheat Sheet Commands for SQL Injection Attacks + PDF & JPG
It covers installation, basic usage, ip address. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits.
SOLUTION Sqlmap cheat sheet Studypool
It covers installation, basic usage, ip address. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection.
Cheatsheet para SQLMap Security By Default
A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities. It covers installation, basic usage, ip address. Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits.
Use Our 20+ Custom Tools To Map The Attack Surface, Find Security Issues That Let You Escalate Privileges, And Use Automated Exploits To.
Learn how to use sqlmap, a penetration testing tool for databases, to check for sql injection vulnerabilities. It covers installation, basic usage, ip address. A cheat sheet for sqlmap, a tool for testing and exploiting sql injection vulnerabilities.